Hello, fellow Google Cloud Platform engineers and developers! Have you ever loved a toolset so much, but there’s just one aspect about it that gives you pause? That's how some people feel about Cloud Run. We like that it allows us to deploy containerized apps and gives us a nice URL that can be used for our app's UI. However, by default, anyone on the internet can access that URL, and that can be a security risk.
Restricting access to your Cloud Run application
Today, we would like to share with you a solution that will give you the ability to restrict access to your Cloud Run application via Google Cloud Platform (GCP) Identity and Access Management (IAM). This approach allows you to manage user access to your app in a way that is:
- Safe
- Secure
- Simple-to-use
- Centralized
- Cost-efficient
How We’ve Used This Solution to Improve ROAS
At Adswerve, we frequently leverage this approach to build applications for marketing data analysis tools. Our typical implementation process involves:
- Building the Application: We develop data science apps, often using Streamlit, a powerful interactive tool for visualizing insights. These applications often showcase results from complex analyses, such as media mix models.
- Deployment: The application is deployed to Cloud Run on Google Cloud Platform (GCP).
- Secure Access Management: We use Identity and Access Management (IAM) to securely manage and share access to the app, ensuring only authorized individuals can view and interact with it.
This approach allows us to create powerful marketing analysis tools while maintaining a high level of security and access control.
Versatility Across Domains
This solution isn't limited to marketing. It works for any field needing secure data analysis. HR, IT, Finance, and other departments can benefit. The same security principles apply across all areas. You can create safe, interactive apps for various business needs. Sensitive data stays protected, yet accessible to the right people.
Typical Steps to Implement This Solution
Our solution is using Identity-Aware Proxy (IAP). The setup requires a few steps, but it is well worth it.
The high-level technical setup is the following:
- Reserve an IP address
- Associated a domain with the IP address
- Route traffic from the domain to the Cloud Run service
- Share the Cloud Run service with specific individuals
The Solution in Practice and Managing Access with IAM
Let's take a look at how this solution works in practice.
Your application will be accessible via a URL in the format {ip_address}.nip.io, where ip_address is the static IP you've reserved for your Cloud Run application. To manage access, you'll use the IAM interface in GCP. This screen allows you to control who can access your application:
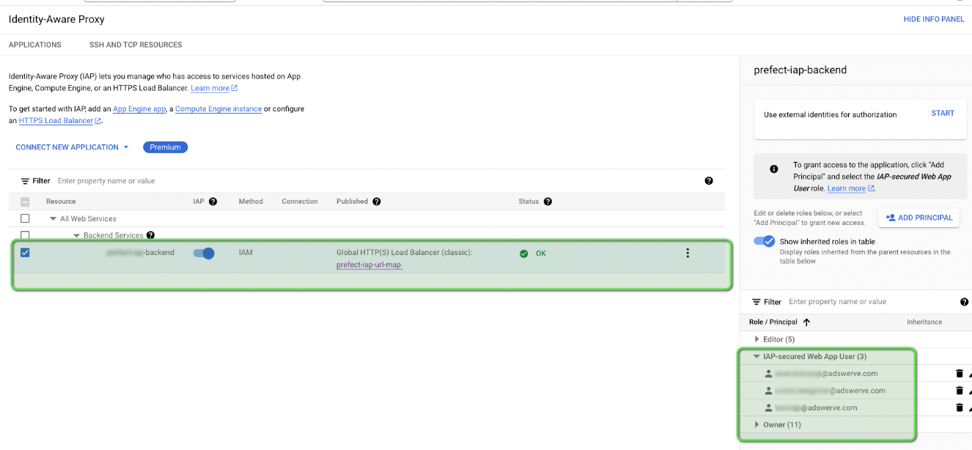
Here, you can add users by entering their email addresses. Once added, these users will be granted access to the application.
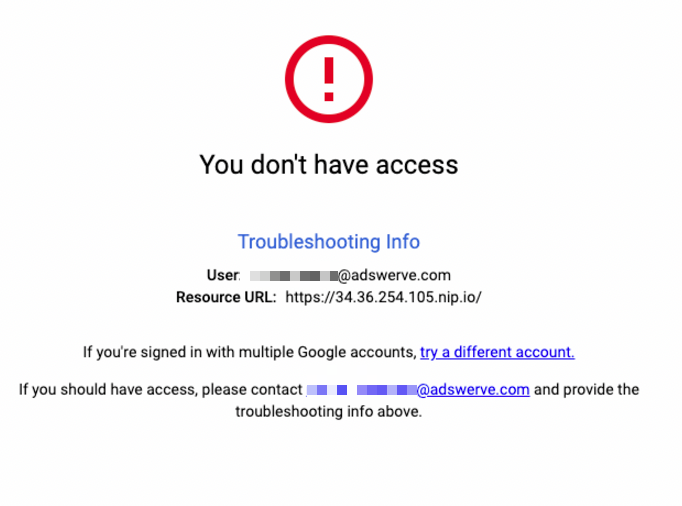
If someone does not have access to your application and they try to access the application via the {ip_address}.nip.io URL, they would get an access denied error.
More Details
Interested in more details? There's a Google Codelab tutorial on the topic. We would like to give credit to this tutorial: it has been the source of the code that we used for the IAP solution.
Secure Serverless Application with Identity Aware Proxy (IAP)
And there’s a video on securing Cloud Run apps:
Cloud Run user auth for internal apps
Adswerve believes in open-source development and giving back to the developer community. We are excited to announce that the IAP solution is open-sourced by Adswerve and available on GitHub. You can follow the instructions in the README to secure your own application.
Please check out the solution here: https://github.com/adswerve/secure-cloud-run-app-with-iap.
Ready to get secure? Reach out to our team for expert assistance.




